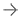
Networked medical devices at a health care provider and their vulnerability to cyber attack, as seen in a screenshot of a display created by the Medigate platform. Image courtesy of Medigate
Cybersecurity is being defined by a kind of arms race.
On one side are the hackers with malware, some off the shelf, some custom made to create chaos in healthcare. On the other are cybersecurity defenders that try to keep malware at bay with shields and intrusion detectors.
From the Cybersecurity Command Center and in the Innovation Live area on the exhibit floor of the annual meeting of the Healthcare Information and Management Systems Society (HIMSS), a cybersecurity firm called Medigate showcased a hardware-software platform that can help health care providers defend against hackers. When installed on medical device networks, the platform can detect early signs of attack and potentially harden vulnerable equipment.
In a pre-HIMSS interview with Imaging Technology News, the company’s chief executive emphasized that, before this can happen, the information technology team and administrators of healthcare provider must understand its network of medical devices. The Medigate technology is specifically designed to make interconnected medical devices visible, said Medigate CEO Jonathan Langer. “It is the crucial first step” toward strengthening networked medical devices against cyber attack.
The company, which is headquartered in New York and conducts R&D in Israel, has identified tens of thousands of devices for dozens of health care systems, many in the U.S. and Canada. Corporate partners include Palo Alto Networks and Cisco.
Medical devices are most vulnerable, Langer said, if security flaws in their operating systems have not been adequately patched. This may be so because security patches, provided by the maker of the operating systems, were not adequately installed or because the software maker had stopped developing such patches because the operating systems had become obsolete.
Unpatched medical devices are common. And, if these devices are compromised, the impact can be devastating to both the institution and its patients.
“All of a sudden a medical device or an imaging device can be unavailable,” he said. “That can have a huge impact on a hospital’s operation.”
And this could be the least of the hospital’s problems. Cyberattackers may infect a hospital network with ransomware, which encrypts data, holding it hostage until the hospital pays for decryption. Alternatively, the attacker may be searching for patient information stored on archives.
“Cyber attackers may be looking for weak links in the network to reach this information,” Langer said. “So it can pivot from imaging (scanners) to the PACS, which holds an abundance of data, or to the EMR, which is a huge repository of highly valuable data.”
How Medigate Fights Cyber Crime
Langer got interested in cybesecurity while serving with the Israel Defense Forces. He later worked as vice president of technology at New York-based CyGov, which provides cyber defense solutions. Now, as the leader of Medigate, which he co-founded, Langer is warning the medical community about devices that are particularly vulnerable to attack — and how the protection for these devices can be improved.
Medigate makes a hardware-software combination — called, simply, the Medigate platform — that can mitigate the danger. The platform, which has both on-premise and cloud components, can be fine tuned to the operation of the healthcare provider.
When installed, it looks for the kind of behavior that signals an ongoing attack — for example, an incubator in the neonatal intensive care unit trying to communicate with an MRI scanner. The concern in this case would be that malware might have turned the incubator into a digital zombie or bot with the mission to infect or disable the MRI.
It also looks for subtle signs of suspicious behavior. These might, for example, look innocuous, digital traffic between a device and its manufacturer. Yet, such traffic might be the result of a successful cyber attack on the manufacturer.
“We alert the hospital to any remote connectivity so it is up to them from a policy perspective to either approve or disapprove of (the contact), he said.
Making Medical Devices Visible
Before the software can detect such threats, it maps all the interconnected medical devices. A large hospital may have a thousand or more of these devices, each of which exhibits a clearly visible “fingerprint,” Langer said — if you know where to look.
“Our discovery process gives us a good understanding of exactly what medical devices are installed and what their technical attributes are,” he explained.
The software can determine the make and model of each medical device on the network, as well as its operating system; current software version; and whether its security is at risk.
Not only does this map provide the basis for detecting the early signs of an attack, it identifies networked devices that Medigate can harden. Once vulnerable targets are found, Medigate can install “compensating controls” to help secure them.
Although nothing can completely protect “unpatched” medical devices, for example, the compensating controls from Medigate provide an additional layer of security. This may be achieved by segmenting the vulnerable devices or establishing additional firewalls for their protection.
Langer said he hopes people attending HIMSS will realize that enormous value can be derived simply by mapping networked devices. Identifying vulnerabilities must be done, if attacks are to be blunted.
“Network visibility is really the fundamental foundation of any cybersecurity program specific to medical devices,” he said. “Without that visibility, you’re just chasing a ghost.”
Related content:
How to Boost Cybersecurity in Medical Imaging
Cybersecurity Threats in Medical Imaging
Medical imaging systems need more cybersecurity
Editor's note: In preparation for the upcoming HIMSS (Healthcare Information and Management Systems Society) Conference on Feb. 11, contributing editor Greg Freiherr begins the show coverage with this exclusive podcast and accompanying blog. This is the final podcast in a series of three. You can listen to the first podcast, Hear and Now: How to Boost Cybersecurity in Medical Imaging, here. You can listen to the second podcast, Hear and Now: AI and Imaging, Your Data as Strategic Asset, here.



 February 13, 2026
February 13, 2026