Feb.
Cybersecurity
This channel page on cyber security includes news and new technology to prevent cyber attacks and hackers from gaining access to electronic medical recored (EMR) data, or illegallly accessing implantable wireless cardiac devices.
Feb. 4, 2026 —The HIMSS Global Health Conference & Exhibition has announced that acclaimed actor and philanthropist ...
As radiology practices shift toward cloud-based platforms and integrate AI-powered tools, will practices become more ...
Aug. 07, 2025 —- New research by European cybersecurity company Modat revealed more than 1.2 million internet-connected ...
Radiologists may not consider imaging systems to be at high risk of cyber attack. But it is for exactly this reason that ...
HIMSS will be presenting a webinar on "Addressing the Changing Data Demands of Next-Gen Healthcare" on Nov. 13, 2024 at ...
HIMSS will present a two-day Healthcare Cybersecurity event next month in Washington, D.C. The Healthcare Cybersecurity ...
June 19, 2024 —Karamba Security, a world leader in end-to-end product security, today announced the signing of a ...
Join Chris Toth, president, Oncology Systems Americas, for a look at Varian’s new product introductions and major ...
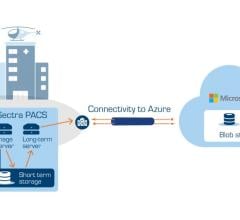
June 4, 2024 — International medical imaging IT and cybersecurity company Sectra has launched a new diagnostic IT module ...
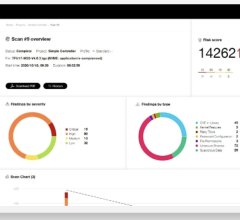
May 13, 2024 — In the wake of the cybersecurity breach targeting the prominent healthcare system Ascension, a new study ...
April 25, 2024 — International medical imaging IT and cybersecurity company Sectra has signed two contracts to provide ...
April 10, 2024 — The American Medical Association (AMA) released informal survey findings (PDF) showing the ongoing ...
March 14, 2024 — The American Medical Association (AMA) has issued a new letter to federal officials in which it praised ...
March 8, 2024 — The following statement was issued by the American Medical Association (AMA) on behalf of Jesse M ...
In the March/April issue of ITN, you will find a strong focus on information technology as we continue to track its ...
March 6, 2024 — As the cyber-takedown of Change Healthcare has forced medical practices to go without revenue for a ...
August 22, 2023 — International medical imaging IT and cybersecurity company Sectra will provide Sectra One Cloud, its ...
July 31, 2023 — The American College of Radiology (ACR) announced the ACRedit Plus and the National Radiology Data ...
The theme of this year’s Healthcare Information and Management Systems Society (HIMSS) Global Conference and Exhibition ...
April 20, 2023 — Today’s healthcare industry faces multiple challenges -- looming clinician shortage, technological ...
This year at HIMSS, the theme is Health That Connects + Tech That Cares, and cybersecurity is indeed a part of this ...
April 17, 2023 — Kicking off day one of the Health Information and Management Systems Society Global Health Conference ...







 February 09, 2026
February 09, 2026 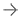









![The following statement was issued by the American Medical Association (AMA) on behalf of [Jesse%20M.%20Ehrenfield,%20MD,%20MPh]Jesse M. Ehrenfield, MD, MPh, President of AMA.](/sites/default/files/styles/feed_medium/public/GettyImages-1599973349.jpg?itok=lsZY16MU)